ctx->lectures->lecture2
How the Net Works, Networks
Networks
In this session we introduced some very basic networking ideas and setups. The most common types of any planar network of nodes to connect is displayed below.
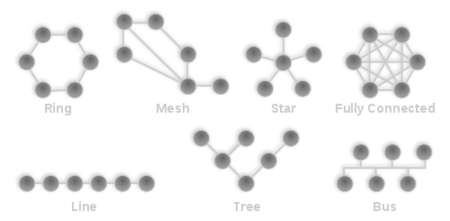
Internet noawdays as it came to be, seems an almost fully connected network. The interesting thing though is that apart from the physical connection, we implement protocols that define the behaviour of network flow in our fully connected graph.
Protocols
Protocols define the way data is transmitted. But since computers are machines, we need both hardware protocols (the media layers, things done on circuitry: Physical, Data Link, Network) and software ones (Transport, Session, Presentation and Application).
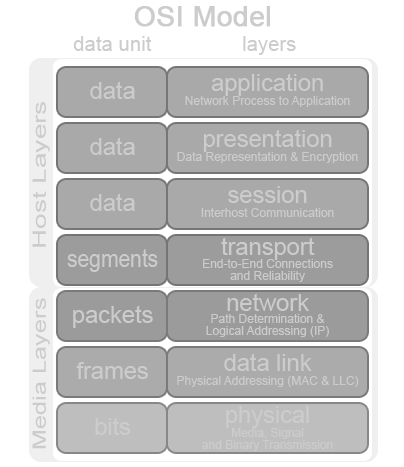
TCP/IP
TCP provides acknowledge connection-oriented communications and provides guaranteed delivery proper sequencing and data integrity checks. If errors occurs during transmission, TCP is responsible for retransmitting the data back. FTP which stands for File Transfer Protocol is an example of a TCP/IP service that depends on TCP.
IP is Internet Protocol and is an unreliable connectionless protocol. This means that the internet protocol does not verify that a specific packet of data has reached its destination. The sole function (or role) of the IP protocol is to transmit TCP/IP. Where TCP is there to check that the information went through. Think of this: a truck driver has to deliver 50 tons of paper to a paper company. The driver is TCP. The load is IP. The driver is there to make sure that the load gets to the paper company.
ThreeWay (handshake)
We already said that TCP ensures the integrity of our network session. So it records the progress of our communication by having a number that is increased after the completion of each dialogue. To start the connection a handshake ensures the initial "agreement".
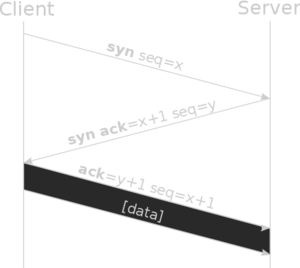
After that they keep ACKnowledging and increasing the number, until one sends FIN (end) or RST (reset). Now if a packet gets lost, by either endpoint, it can request from his partner to retransmit it.
Private IP ranges
The Internet Assigned Numbers Authority (IANA) has reserved the following three blocks of the IP address space for local networks:
10.0.0.0 - 10.255.255.255 172.16.0.0 - 172.31.255.255 192.168.0.0 - 192.168.255.255
The most common use of these addresses is in residential networks, since most Internet Service Providers (ISPs) only allocate a single routable IP address to each residential customer, but many homes have more than one networked device, for example, several computers and a video game console. In this situation, a NAT gateway is usually used to enable Internet connectivity to multiple hosts. Private addresses are also commonly used in corporate networks, which for security reasons, are not connected directly to the Internet. Often a proxy, SOCKS gateway, or similar devices, are used to provide restricted Internet access to network-internal users. In both cases, private addresses are often seen as enhancing security for the internal network, since it is difficult for an Internet host to connect directly to an internal system.
NAT
NAT is the process of modifying network address information in datagram (IP) packet headers while in transit across a traffic routing device for the purpose of remapping one IP address space into another. Most often today, NAT is used in conjunction with network masquerading (or IP masquerading) which is a technique that hides an entire IP address space, usually consisting of private network IP addresses behind a single IP address in another, often public, address space. This mechanism is implemented in a routing device that uses stateful translation tables to map the "hidden" addresses into a single IP address and readdresses the outgoing Internet Protocol (IP) packets on exit so that they appear to originate from the router. In the reverse communications path, responses are mapped back to the originating IP address using the rules ("state") stored in the translation tables.
BGP
Important nodes that connect vast networks with other vast networks (central internet routers) need extra protocols if they are to be efficient. The Border Gateway Protocol (BGP) is the protocol backing the core routing decisions on the Internet. It maintains a table of IP networks or 'prefixes' which designate network reachability among autonomous systems (AS) (Europe/Greece are one larger and one smaller autonomous systems).
Application Layer
OK, all these are really interesting but mostly non important. How does a UNIX system access the whole Internet? Since everything in UNIX is a file (like devices which are interfaced as files), and specific system functions that operate on these device files (like socket() and connect()) can create even more files, our "virtual" internet session is represented as a file (that we just write to and read from). We can understand why BSD sockets (this framework) took the early Internet by storm and is even today the de facto way to exchange data on any Operating System (yes, even Winlose95) ;). To know how to control these things from your code, you must read the excellent book of Richard Stevens: Unix Network Programming.
Finally, when we said fully connected, we meant it. Here is a part of it visualised by the Opte project.

Happy Hacking ;)
dsp@
